Unveiling Domain Spoofing: The Mechanics Behind This Deceptive Practice
Nasser Oudjidane
•
Co-founder
•
August 21, 2024
•
5 min read
Safeguard your ad budget from domain spoofing fraud. Learn what it is, how it works, and actionable strategies to protect your campaigns.
To run a successful advertising campaign, it's crucial for advertisers to maximize their ad budget and connect with genuine audiences. However, fraudsters pose a constant threat, seeking to siphon off portions of that budget.
One prevalent fraud tactic is known as "domain spoofing." In this article, you'll discover what domain spoofing entails, its various manifestations, and actionable strategies for advertisers to safeguard their ad budgets against it.
What is domain spoofing?
Domain spoofing is a prevalent tactic employed by fraudsters to divert ad budgets. It entails crafting substandard websites that mimic well-known ones, often replicating them almost identically. At first glance, these counterfeit sites are indistinguishable from the originals.
Fraudsters submit these fake sites to various ad networks, portraying them as premium inventory, and populate them with display and video ads. They then utilize bot traffic to engage with the ads, ultimately aiming for a payout.
The method seems straightforward and efficient, and indeed it is. Advertisers pay for what appears to be premium traffic, only to realize no conversions or desired branding effects.
There are several motives behind domain spoofing:
- Committing ad fraud by generating low-quality or automated bot traffic
- Concealing the traffic's origin, particularly if the site hosts illegal or undesirable content
- Facilitating phishing attempts
- Propagating malware or spyware
- Harvesting personal information
What are the various forms of domain spoofing?
Domain spoofing can be categorized into simple and more intricate techniques.
Simple domain spoofing methods entail replicating websites exactly and hosting them under a new domain.
More sophisticated methods involve spoofing email addresses, disseminating malware via websites, or pilfering personal data.
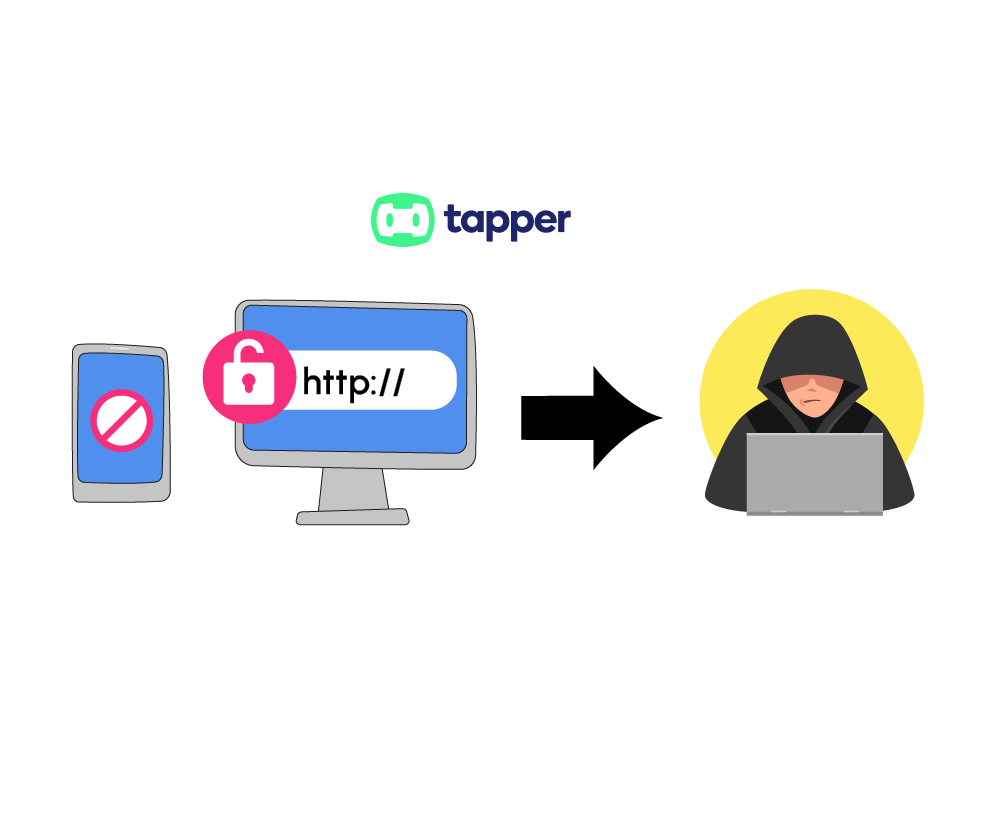
Website / URL Spoofing
This is the most basic form of domain spoofing. Fraudsters provide the ad server with the URL of a genuine, high-value publisher. Consequently, advertisers believe their ads are being displayed on a legitimate site like forbes.com, when in reality, they appear on a counterfeit website.
Another tactic employed by fraudsters involves leveraging Unicode characters within the domain. Unicode, an international standard for character encoding, assigns a unique number to each character in all languages and scripts, ensuring their accessibility across various platforms, programs, and devices.
For instance, the letter "h" closely resembles the Unicode character "һ" (Shha in Unicode). Fraudsters exploit this resemblance by registering domains for their bogus websites that closely mimic the domain names of legitimate sites.
A catalog of visually similar Unicode characters can be found here.
Cross-Domain Embedding
This technique employs iFrames, which are HTML elements used to integrate external content into a website. This content can include images, videos, or even entire websites.
By embedding a respected website within an iFrame on a counterfeit site, it can give the impression to advertisers that their ads are being displayed on the reputable site.
Malware
Fraudsters can utilize infected apps or browser extensions to inject ads into websites and apps without the user's awareness.
Here's how it typically operates: when a user launches an infected app, invisible advertising banners load in the background and are automatically clicked on. Each click on an ad generates revenue for the fraudsters.
One example of fraud exploiting this method was Zacinlo. This malware executed various fraudulent activities, including browser redirects, automated clicks on online ads in hidden browser windows, and substitution of legitimate ads with those of the attackers to collect ad revenue.
.png)
Why does domain spoofing remain a significant issue in 2024?
Simply put, domain spoofing persists because it offers fraudsters a lucrative opportunity to generate substantial profits rapidly.
Copying an existing website, placing ads on it, and then earning money through bot traffic and fake clicks has become increasingly automated and accessible.
For instance, in 2017, the Financial Times conducted an investigation revealing the prevalence of fake domains masquerading on various advertising networks. The findings indicated that the value of fraudulent ad inventory amounted to approximately $1.3 million monthly.
One notable case is Methbot, a major ad fraud scheme that operated a few years ago. Methbot orchestrated up to 400 million fake video ad views, 6,000 domains, and over 250,000 URLs daily at its peak. This scheme enabled fraudsters to earn as much as $3 million per day, primarily through domain spoofing.
Reviewing the significant ad fraud cases in recent years underscores the prominence of domain spoofing as a favored technique among fraudsters, resulting in substantial earnings for numerous perpetrators.
Pointers for spotting domain spoofing, a practice that can swiftly deplete your advertising funds.
Review reports manually
Check for irregularities in domain names and URLs. These may include extra characters or numbers, with particular attention to Unicode characters that resemble other letters. While manual inspection is thorough, it can be time-consuming, especially for extensive advertising campaigns. Therefore, it's advisable to initially place ads only on approved domains listed in an Allow/Inclusion list.
Implement Ads.txt
Introduced by the IAB Tech Lab in May 2017, as part of the Authorized Digital Sellers project. This initiative targets various forms of ad fraud, including domain spoofing and unauthorized inventory resale.
Ads.txt is a straightforward text document that specifies which companies are authorized to sell digital ad space on a particular domain. Because it can only be managed by the domain's webmaster, the information in the file is deemed valid and trustworthy.
While Ads.txt cannot entirely eliminate domain spoofing, it offers an additional layer of security, provided it is correctly implemented and regularly updated by the publisher. Therefore, it's advisable to advertise only on domains with an Ads.txt file in place.
Use Fraud Detection Software like Tapper
Although manual methods and ads.txt implementation offer some level of protection against domain spoofing, they have limitations and may not safeguard against all forms of attack, such as cross-domain embedding.
To enhance your defense against domain spoofing and other fraudulent activities, we strongly advise employing fraud detection software.
Our solution, fraud0, provides real-time protection against domain spoofing by analyzing various domain characteristics. For instance, our system can identify whether an ad is displayed within an iFrame, including reporting on both the iFrame and the main URL. Additionally, it verifies whether the transmitted URL corresponds to the actual URL where the ad was served.
Moreover, our system safeguards your brand reputation by preventing your ads from appearing alongside unsafe or inappropriate content, such as fake news, radical political material, terrorist-related content, or sexually explicit websites.
Stop Paying for Fake Traffic
Run a 30-day Tapper trial to set your baseline CPA, block invalid traffic in real time, and receive a final report comparing your CPA before and after protection.
Get your free trial